
Interactive, entertaining & up-to-date
IT and cyber security training for employees
Interactive, entertaining & up-to-date

2,000+ customers trust in our security awareness trainings, from start-ups to large companies
Top quality content
We don't just create e-learning courses, we sustainably convey security know-how.
Modular system plus phishing simulations
Choose from over 40 modules on cutting-edge topics:
Would you like to discover our cyber security training courses in a live demo and discuss your requirements in a personal meeting?

Over 40 modules, always up-to-date, constantly growing
How do attackers proceed?
Exciting short movie "Ananomie of a cyber attack" with physical access, phishing and social engineering over the phone. Which groups of attackers pursue which goals? 10 min with short movie.
Why cyber security?
How does cyber security work? Why technology is not enough on its own. What important role does the human firewall play? 4 min with video.
Cyber security for managers
The special role of the manager in cyber security: team leader, role model & information owner. The “magic triangle” of easy, cheap and secure. The specific tasks of the manager in everyday life. 9 min with video and interactive exercises.
Email & Phishing
How can you recognize and fend off phishing emails? How can you correctly decode the link in an email? Where do you report a suspicious e-mail? With video and interactive exercises.
Microsoft 365-Phishing
What do attacks on Microsoft 365 logins look like? How can they be detected and defended against? How secure is MFA with Microsoft 365? With video and interactive exercises.
Phishing next level
The clever tricks of attackers unmasked: QR codes, 2-step phishing, social engineering on the phone and via teams. With video and interactive exercises.
Ransomware
How do ransomware attackers proceed? Why is the first victim often a user? How can you protect yourself? With video and interactive exercises.
Dangerous file extensions
Which file extensions in email attachments are harmless and which are dangerous? Why can Office documents in particular be very dangerous? With video and interactive exercises.
Viruses & malware
How many viruses and malware exist for which end devices? Where do you need a virus scanner and where not? Which software should you use privately? With video and interactive exercises.
Cyber incident
What is a cyber incident? What do you do in the event of an incident? Where do you report the incident? And what happens next? With video and interactive exercises.
Secure passwords
How are passwords cracked? Why are trivial passwords hacked in seconds? How do you create secure passwords that you can remember? With video and interactive exercises.
Admin passwords
Why do privileged passwords need to be particularly strong? Why do they have to be different? And how do you deal with privileged passwords? With video and interactive exercises.
Password management
How secure are password managers? Should you use password managers? If so, which one? Where are the limits? With video and interactive exercises.
Multi-factor authentication
What is multi-factor authentication? Why is it fundamentally important? Is MFA phishing-resistant? Which solutions can be used? With video and interactive exercises.
Local admin rights
What are local admin rights? Why do security experts consider local admin rights to be bad? What responsibility is involved with these rights? With video and interactive exercises.
Identity & access management
What is identity management? Which identities are managed centrally by IT and which are managed by admins in the business departments? What responsibility does this entail? With video and interactive exercises.
Attackers manipulate their victims with pressure, a need for help and a plausible story. This learning nugget provides the necessary knowledge to recognize social engineering scams and react correctly. With video and interactive exercises.
Many companies have already transferred large sums of money to fraudsters. This learning nugget explains the attackers' scam and provides practical tips for protection. With video and interactive exercises.
What are attackers looking for on site? How can you increase information security through your own behavior? Clean desk, clear screen, safe disposal, correct handling of visitors. With video and interactive exercises.
Why are confidential conversations in public dangerous? Is the hotel a “safe” place? Should you use public WLANs? With video and interactive exercises.
How do you access company data on the move? Why shouldn't anyone else use the company device? What should you watch out for during web meetings or phone calls? With tips for private devices at home, video and interactive exercises.
What distinguishes public cloud offerings from your own company's cloud services? Why does company data have no place in public cloud services? With tips for secure surfing at home, video and interactive exercises.
How can you increase privacy on social media? Why should you always check your privacy settings and not post company information? What rules apply to company data? With video and interactive exercises.
Why do security experts have such big problems with software and apps from the Internet? Is it really that dangerous? What can happen and what does “shadow IT” have to do with it? With video and interactive exercises.
How does a generative AI like ChatGPT work? What are the challenges involved? Can the results be trusted? How can you use these systems safely? With video and interactive exercises.
How does AI work? What challenges are associated with genetic systems? What does the AI regulation want? How can AI systems be used safely? And how do you get the best results? With video and interactive exercises. Learn more...
What does information security do? What are the protection goals? How do you manage it all? Who is responsible for what? And what role does each individual person play? With video and interactive exercises.
What does PCI DSS mean, why is it so important and what are the specific requirements for handling credit card data? With video and interactive exercises.
What is BCM and why is it fundamentally important? What can cause an emergency and how can an organization prepare for it? What should be done in an emergency and what role does each individual play? With video and interactive exercises.
How do organizations become resilient? What exactly does NIS-2 want? What does it mean for managers? And what does it mean for employees? With videos and interactive exercises. Learn more...
What does DORA require? What goals does it pursue? What are the main pillars of DORA? And why does the law really make sense? With video and interactive exercises. Learn more...
How does AI work? What challenges are associated with generative systems? What does the AI regulation want? How can AI systems be used safely? And how do you get the best results? With videos and interactive exercises. Learn more...
What pitfalls lurk in MS Teams for the security of information? Who should become a member of a team? Who can access which files? With video and interactive exercises.
Is Apple iOS more secure than Google Android? Where do you need a virus scanner and where not? Are company devices better protected? With tips for private mobile devices, video and interactive exercises.
Why does information need to be classified? Who does this? In which tool? According to which criteria? And what happens when information is assigned to a confidentiality class? With video and interactive exercises.
How do you classify information in the right confidentiality class? Who is responsible for this? And what does this classification mean for the handling of the information? With video and interactive exercises.
"The security awareness training platform from IS-FOX has exceeded our expectations. The practical training, user-friendly design and high-quality content - including up-to-date modules such as NIS2, whistleblowing and due diligence in the supply chain - offer real added value for our company. Our employees are now well prepared to recognise security risks and act with confidence. An unreserved recommendation!"
Dirk Wocke, Compliance Manager (ISO / DPO)
indevis IT-Consulting and Solutions GmbH

"We are impressed by IS-FOX’s fast, professional approach and their incredibly helpful team. Their security awareness trainings integrated seamlessly into our existing LMS and deliver practical, high-value content. A competent and reliable partner we can confidently recommend."
Johannes Götz, Head of IT
nosta GmbH

For small and medium-sized companies.
Just select licenses, invite participants, done! The rest works fully automated: invitations, reminders, tracking. This is how training works today.
For companies with their own learning management system (LMS).
You have your own learning management system or need customizations? No problem! Our courses will become “your” course in no time at all... with integration of the policies and the logo.



Impressive and engaging. Recommended for everyone in a company.

IS-FOX creates real behavioral change. We are excited.

The IS-FOX awareness platform is perfect for us.
Because we are a subject specialist, didactics expert and agency – all in one.
Thanks to our security consultants, incident response specialists and data protection experts, we know what's really important and what isn't. That's why our content is not only entertaining but also “audit-proof”.
We take the complexity out of topics and get right to the point by removing unnecessary jargon: crisp, understandable, comprehensive, always with practical tips - which is exactly why it sticks for longer.
Our multimedia team creates all IS-FOX products in-house: from storyboard, animation and graphic design to production. That's why we can also individualize excellently and react to new developments at lightning speed.
FAQ
What distinguishes a good e-learning, explainer video or webinar from a bad one? The script and the messages. If the basis isn't right, the rest won't work.
Script and messages are probably our greatest strengths. We focus on the essentials, always ask ourselves “why do I actually need to know this as a learner?”, throw out unnecessary blah-blah and foreign words and get to the point very quickly with a simple, comprehensible “call to action”. The participants love our content for this and regularly give us excellent feedback.
Addressing the right target group is very important for us, especially as part of an awareness campaign. Take a look at our know-how article on training the often forgotten IT target group.
We offer a wide range of content for target group-specific training, which can be put together flexibly and designed according to different criteria:
Function in the company: For example, dedicated training for managers, for all employees, etc.
Department / role: Special training for IT professionals such as developers or IT administrators, production employees, people in the board/finance area, etc.
Level of knowledge: Basic training, advanced training or training for people with a specialization, e.g. processing credit card data, people with privileged rights, or people who are frequently on business trips, etc.
All-in-one: training courses with pre-test. If you pass, you're through. Or training courses with refresher paths: Have you attended content before? Then take the refresher path!
We will be happy to advise you on putting together the right training for your target groups.
Yes - participants can have a certificate issued. Either through their company's learning management system or through the course, as required.
Of course, we always have our ears to the ground and keep an eye on changes, both in the legal situation and in company practice. If there is something to change, we update accordingly.
As part of our cloud service, these updates are included in the annual fee. With a purchase license, we inform you about the new version and you decide for yourself whether you want to update or not. However, the update price is so attractive that you can hardly refuse.
Other courses that might interest you
E-Learning knowledge from our blog

How to repackage familiar GDPR content into exciting online courses.

Find out how companies can properly motivate their employees to complete an e-learning course on cyber security, data protection or compliance.
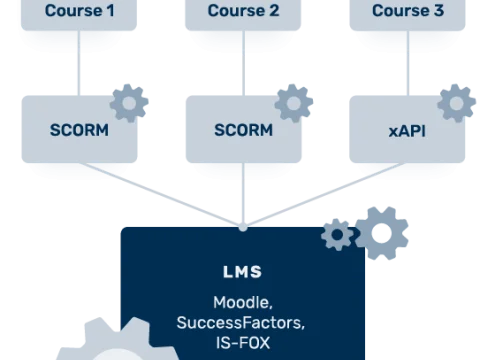
In this article, we explain the technical terms Scorm, LMS and e-learning course.