
IT security for hospitals
Cyber security in the medical sector
Cyber Security E-Learning-Kurse speziell für medizinisches Personal und für Klinken.
IT security for hospitals
Cyber Security E-Learning-Kurse speziell für medizinisches Personal und für Klinken.

2.000+ trust in our cyber security trainings – from startups to large companies
Custom solutions
The e-learning courses have been developed by real cyber security specialists, with content and examples from the clinical environment. You can either choose one of our "best practice" compilations or customize your cyber security training - both of course adapted to your guidelines and corporate design.
You can run the finished online training course in your own learning management system in the company or in our cloud, naturally from a German data center in accordance with the EU GDPR.
Need another language?
You can watch the video above in German. Our e-learning courses however are available in many other languages on request - from Spanish and French to Chinese or Russian. Which language do your employees need? Feel free to contact us - we will find the right solution for your team!
Really great training! Super videos! Short, concise and very easy to understand explanations. My compliments!
Clinic management
Very valuable.
Sensitizes the entire team!
Owner of a private practice
Learned a lot plus interactive and exciting exercises! Thumbs up!
Intensive care nurse
Wie funktioniert E-Learning?
Falls Sie erst einmal verstehen möchten, wozu ein Lernmanagement-System überhaupt da ist und warum diese Systeme alle Scorm sprechen, empfehlen wir Ihnen unseren Know-How-Artikel E-Learning Grundlagen.
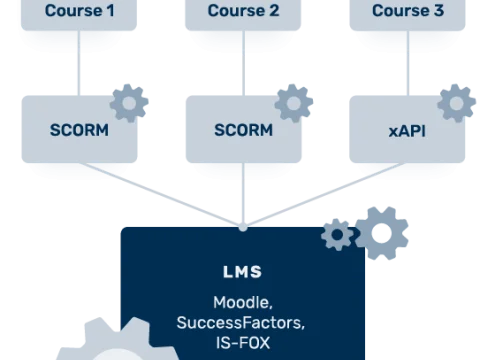
In this article, we explain the technical terms Scorm, LMS and e-learning course.
Get a free demo account for the other chapters and let's talk about your company's needs in a web meeting.

Unsere top-aktuellen und modernen Datenschutz Online-Schulungen machen Deine Mitarbeitenden fit für die DSGVO.

Arbeitsschutz im Unternehmen einfach erklärt und auf den Punkt gebracht. Als E-Learning mit Zertifikat. Jetzt informieren und Schulung buchen!
IT-Security-Training für Administratoren mit interaktiven E-Learnings und eigener Hacking-Umgebung.

Wir zeigen, wie man Mitarbeitende richtig motiviert.

So werden bekannte DSGVO-Inhalte in spannenden Online-Kursen neu verpackt.

In diesem Artikel erklären wir die Fachbegriffe Scorm, LMS und E-Learning.