2.000+ customers place their trust in us – from startups to large companies
Secure your software
Secure development is not a product, it's a concept. If development teams comprehensively implement tips and measures from our Cyber LAB training courses for developers, they will significantly increase the security of software - during development and operation.
Minimize human error
The damage caused by careless users is annoying but the damage caused by careless developers can quickly become a disaster. Our cyber security training courses create an understanding of secure development and convey the necessary conceptual knowledge for secure software.
Turn DevOps into DevSecOps
Developers who've been trained with our Cyber LABs meet security standards far more reliably, they use threat modeling, use key vaults and an automated security check in their CI/CD pipeline because they understand the necessity and purpose behind it.
Security training for developers is much more challenging than traditional employee training. The effects of non-security-conscious behavior cannot be presented in a simple, striking way like somebody clicking on a virus-infected attachment. Developers need considerably more background info about the attackers' approach in order to understand the effects of their own behavior.
The necessary behavioral changes have much greater impact on the developer's everyday life than conventional security measures. Developers need to understand the importance of these measures and, above all, that their own changed behavior is fundamentally important.
This understanding is best developed in “hands-on” workshops with a LAB environment for practical hacking exercises. However, such workshops can quickly become expensive and are almost unfeasible for globally active organizations. E-learning courses, on the other hand, remove this limitation. They can be held at any time and from any location and are very cost-efficient. However, pure e-learning courses lack the practical exercises and a coach who can also explain the background. We bring both together to create efficient training for sustainable behavioral change.
50% faster learning success
With Cyber LABs we reduce training time by 50% compared to similar live events without compromising the learning success. In the past, trainers have needed up to eight hours to cover the same content in person. Why? Because of regular breaks, waiting times until all participants had started the LABs and typed in the commands correctly. In our Cyber LAB, two virtual trainers guide you through the program in a flexible way and each participant can complete the LABs at their own pace.
Created by experts
The Cyber LAB's content is created by security specialists, pentesters, incident responders and developers from HvS-Consulting. The realization comes from our IS-FOX e-learning specialists. The result is a developer training course that conveys secure development in an understandable and varied way – not just “writing secure code” but understanding "security as a concept". Prepared in a way that allows security beginners to follow along easily, while keeping the professionals interested. That's why we often read thing like “Best training ever” in our participant feedback.
Long-term security
There is often a lack of knowledge and/or understanding of security in development. Secure development changes day-to-day work, makes it more complicated in some cases and extends development cycles. Without an understanding of “why” this has to happen, there will be a lack of acceptance among developers and product owners. The Developer LABs create such understanding and convey secure development as a concept, not as a collection of scanners and tools. This creates significantly more security - in the long run.

Intro & let’s hack
Introduction & basics
- How does the Secure Development Training work?
- Why is security so important throughout the software development lifecycle?
LAB exercise
- A bit of hacking to warm you up. Topic: bad exception handling and password cracking.
- The exercise shows what effects even inconspicuous security gaps can have.
Basics
Protection goals in the CIA triad
- Confidentiality
- Integrity
- Availability
Security principles, to meet CIA protection goals
- Don't trust any input
- Keep security simple
- Minimize attack surface
- Implement “defense in depth”
- Use minimal rights
- Be “secure by default”
- Always solve security problems thoroughly
Implementation phase
Authentication
- What mistakes are commonly made during authentication?
- What simple secure development tools can developers use to significantly increase security in this case?
Authorization
- What is the difference to authentication?
- LAB exercise: Access to data via direct object reference
- How can developers prevent such vulnerabilities and what does appropriate access control look like?
Session management
- What threats exist around session management?
- LAB exercise: Taking over a session through session fixation
- How can session management be designed securely?
Input validation, output sanitization and injection
- What is an injection and what forms are there?
- LAB exercise: Data manipulation and deletion using SQL injection
- Which secure development tools can be used to prevent injections?
Cross-site scripting
- What types of cross-site scripting are there?
- LAB exercise: on persistent cross-site scripting
- Which defensive measures are effective?
Cryptography & secrets management
- What types of secrets are there and what forms do they take (“at rest”, “in transit” and “in memory”)?
- LAB exercise: System access via file inclusion
- What is the difference between encryption and encoding?
- LAB exercise: Decoding a password in a config file
- Tips for dealing with secrets
Remote code execution
- LAB exercise: web shell upload
- Why do RCE vulnerabilities have such catastrophic effects?
- How can the “defense in depth” approach within the secure development lifecycle reduce such effects?
Exceptions & error handling
- How do hackers exploit error messages and error routines?
- What should secure error handling look like?
Application logging
- Why is a good logging strategy essential and what should developers better not log?
- LAB exercise: Confidential data in log files
- Tips on how to achieve good logging
Secure networking and infrastructure
- Hackers attack systems, not software. What vulnerabilities are there in transmission protocols?
- Why are hardening and patching not only the task of administrators, but also of developers?
Validation phase
Code reviews
- What security best practices are there?
- When should you perform a source code review?
Automated code analyses
- What are the benefits of automated code analyses?
- Which modules can be analyzed?
Vulnerability scans
- What are the benefits of automated vulnerability scans?
- What are their limits?
Penetration tests
- Why are penetration tests sometimes essential?
Operating phase
Code changes
- How do code changes impact security?
- What measures should be taken?
Configuration
- How dpes configuration impact security?
Patch management
- Who's responsible for patching the systems and to what extent?
- LAB exercise: Exploitation of another RCE vulnerability through an outdated library
Decommissioning
- What steps need to be taken when a system is “end of life”?
Test to conclude
Secure development lifecycle final test
- How much did you remember?
- Multiple-choice questions
- Certificate for download (if passed)
"Very much a straightforward training with lots of examples and very good explanations."
Participant feedback Cyber LAB e-learning for developers
"A very good training course. It was presented in an entertaining way and was a lot of fun in combination with the LAB parts."
Participant feedback Cyber LAB e-learning for developers
"Best in-house "self-service training" I've ever had."
Teilnehmer-Feedback Cyber LAB E-Learning für Entwickler

Cloud security
Cloud security
- Operating models in the cloud
Shared responsibility
- The admin's and the cloud providers respective roles
Tips for the cloud
- Clean account separation
- Securing privileged accounts
- Jump server concept
- Various multi-factor methods
- Private networks and IP restrictions
LAB exercise
- Accessing a poorly configured cloud database through OSINT search
3rd Party Libraries
Risks
- What are the dangers of using 3rd party libraries?
Practical tips for risk reduction
- Reputation checks of developers and repositories
- Continuous use of dependency check tools
LAB exercise
- Attacking software via an unpatched 3rd party library
Single Sign-On
Benefits and risks of SSO
- Benefits and advantages of central identity providers
- Explanation of SSO with Oauth, OpenID Connect and SAML
- Risks of SSO use with weak validation of tokens
- Practical tips for securely signing tokens
LAB exercise
- Undermining single sign-on with a manipulated Oauth token
DevSecOps
The concept
- Why do DevSecOps offer a win-win-win situation?
Automated security checks
- How can functional tests, code scanners, etc. be used to permanently eliminate vulnerabilities?
Infrastructure as code
- Code is code - and therefore susceptible to vulnerabilities
- Tips for secret handling and security checks with IaC
Lab exercise
- Reading secrets from the state of an IaC project
IP and AI
Strictly confidential
- Why can source code be very sensitive?
- How should trade secrets be protected?
Clean separation
- Why should business code not be edited with private accounts?
Healthy doubt
- When is the use of AI in development really beneficial and when is it more of a risk?
Test to conclude
Cloud security & DevSecOps final test
- How much did you remember?
- Multiple choice questions
- Certificate for download (if passed)
Let's talk in person!
Get a free demo access and let's talk about your situation and goals in a web meeting. We look forward to meeting you!
The next steps
This is how you make the most out of your Cyber LAB
Our Secure Development Training for developers creates the right basis for secure application development: product managers, application owners, software architects and developers understand why secure development is fundamentally important and which components are required for it.
However, this enthusiasm for security must then also be properly channeled so that secure development actually has a lasting impact on day-to-day development.
How can this be done? Here you will find our proven best-practice approach, with which you can make secure development a pillar of your everyday development process.
Reason 1
Highly efficient training
By combining an e-learning with a LAB environment, we're able to reach developers all over the world, especially in near-shoring or off-shoring centers. This is fundamental for risk reduction, as many development teams were previously hardly accessible for training at this quality level.
Reason 2
Guaranteed learning success
The main problem with security awareness among developers is the lack of insight and concern. In our Cyber Security LAB e-learning your developers take on the perspective of an attacker and hack through an application in a variety of ways. This creates a very high level of personal involvement and a deeper understanding of why it is so important to be compliant with secure development principles. This is the basis for real behavioral change.
Reason 3
Usable worldwide
Reason 4
Guidelines can be integrated
In principle, our secure development training does not require any individual adaptations. However, you can integrate your own important documents and guidelines (secure coding checklists, crypto systems used, code analyses, etc.) at certain points if you wish. Of course, we will also integrate your company logo and name the specific security contacts.
Reason 5
Fair pricing
The Cyber Security LAB e-learning for developers is licensed per participant. The price for a single participant (including e-learning course, LAB infrastructure, operation, licenses, etc.) is between EUR 80 and EUR 250 net plus VAT, depending on the number of participants, and thus costs merely a fraction of a similar classroom training course, yet delivers virtually the same learning success.
See for yourself!
Would you like to try out the Secure Development Training yourself or find out more? Simply contact us and we'll be glad to help you!
Other training courses that might interest you:
IT security training for administrators with interactive e-learning and hacking environment.

Modern and entertaining IT security trainings protect your company from attacks and their consequences.

Up-to-date and modern online data protection training courses make your employees fit for GDPR. Find out more and book training now!
E-learning knowledge from our blog

How to repackage familiar GDPR content into exciting online courses.

Find out how companies can properly motivate their employees to complete an e-learning course on cyber security, data protection or compliance.
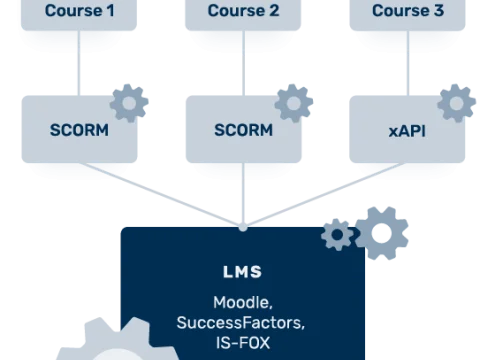
In this article, we explain the technical terms Scorm, LMS and e-learning course.

Everything important about whistleblowing in a 9-minute learning nugget.