
Cyber security: What's important for your IT security
Protecting a company against cyber attacks & threats doesn't have to be a mammoth task. In this article, we'll share some of our most important IT security insights with you.
Protecting a company against cyber attacks & threats doesn't have to be a mammoth task. In this article, we'll share some of our most important IT security insights with you.

The importance of cyber security is increasing with the ever-growing threat of cyber attacks. In Germany alone, the number of companies targeted by a cyber attack was around 17.7 million in 2019 (published by Statista Research Department, 15.12.2022). In the Allianz Risk Barometer, the threat of cyber risks has also taken first place for several years. So there is no question that cyber security has become a massively important issue.
It is also important to understand that cyber attacks and technologies are constantly evolving. While basic concepts such as phishing, social engineering and the likes are perennial favorites, new “phishing scams” or targeted attacks that make use of technological advances, for example in artificial intelligence (AI), are constantly evolving. Vishing, deep fakes and phishing emails generated via ChatGPT are just the beginning.
In this article, we look at the basics of cyber security as well as important developments and focus topics.
IT security protects digital information in technical systems, in other words "everything that has a plug". Typical protective measures include virus scanners, firewalls, backups, e-mail encryption or multi-factor authentication. All these technical measures are designed to ensure that sensitive information does not fall into the wrong hands (confidentiality) and that IT systems are available when they are needed (availability).
IT security is a subset of information security because, unlike IT security, information security is concerned not only with digital information but with all types of information including physical information (e.g., prototypes or printed documents) as well as the "spoken word" (in meetings, telephone calls, etc.). Information security is also more of a comprehensive risk management: Sensitive information is identified, potential threats are determined, and then the appropriate protective measures are derived and written down in security policies. The implementation of these measures in the technical IT systems is the ensuing task of IT security.
And cyber security? This is where it gets exciting. Cyber security is actually just a new word for IT security, but many people now equate it with information security, because a large proportion of attacks on information originate in cyberspace... and because it simply sounds much cooler. :-)
Most of the attack vectors in cyber security mentioned below rely on humans as the gateway.
This is because even if a system is optimally protected (which it rarely is in practice), attackers can still penetrate systems by deliberately deceiving, manipulating or exploiting human vulnerabilities and spread ever further there by lateral movement.
That is why cyber security trainings and general awareness through security awareness campaigns are an elementary component of a security strategy.
'Malicious software' is the generic term for all malware written by hackers to penetrate and damage and/or spy on other people's computers.
A virus is malware that can infect a computer system and make changes to it on its own. Computer viruses, like real viruses, can spread to other systems without the user's intervention and thus cause enormous damage very quickly.
A malware that disguises itself as useful software. When installed, the malware is secretly installed in the background. Most Trojans have a very broad set of hacking capabilities: they can steal or modify files, read messages and chats, turn on webcams and record all keyboard strokes to capture passwords, for example. Unlike viruses, Trojans do not replicate automatically.
A made-up word from the English 'ransom' and software. This malware encrypts computer systems and then extorts a ransom from victims to obtain the key. Ransomware is currently the biggest threat to virtually all businesses, especially APT Ransomware attacks.
A ransomware attack by highly professional criminals. They infect their victims with malware, then penetrate further into the network step by step until, within a few weeks, they have control over all of a company's important IT systems: Databases, backups, email systems, domain controllers. During this time, they steal data from these systems in parallel. When all important systems are under control, they encrypt them and ransom the company with sums in the millions. If they don't want to pay, the criminals additionally threaten to publish all captured data.
Social engineering is the generic term for manipulating and deceiving people in order to obtain confidential data and information. Attackers pretend to be someone they are not in order to trigger actions in their victims, such as entering passwords, opening an attachment, or transferring money to a specific account.
Phishing is a made-up word from "password" and "fishing", i.e. "fishing for passwords". This refers to all the fake websites, e-mails, text messages or the like that criminals use to impersonate a specific person in order to obtain a victim's personal information. Phishing is therefore a variant of social engineering.
Vishing is a further development of the made-up word phishing when it comes to telephone calls, i.e. "voice phishing". Here, too, the aim is to obtain confidential information, but this time via the telephone.
Smishing originates from "SMS phishing", i.e. phishing via SMS. So it's basically phishing, only that the communication channel is a text message instead of an email. Here, too, the victims end up on fake websites or triggered to install malware.
Most of the attack vectors in cyber security mentioned so far rely on people as the gateway. That is why cyber security training and general training through security awareness campaigns are an elementary component of a security strategy.
Another attack vector in cyber security is attacks on IT systems, i.e. servers or applications, for example by hacking or exploiting zero-day vulnerabilities.
However, the widespread division into "attacks on people and systems" is misleading, since the systems are also developed and operated by people.
Our day-to-day experiences often show us:
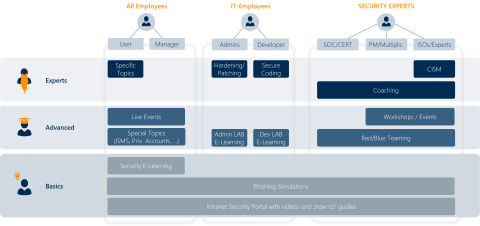
The exploited vulnerabilities in the systems are only rarely "unavoidable", such as when there is simply is no update (security patch) for a vulnerability yet. Much more frequently, hackers exploit vulnerabilities that could have been avoided, if developers and IT-Admins were more aware of security best practices.
Cyber security awareness is urgently needed in IT, perhaps even more urgently than for "normal users", because IT usually works with privileged rights and an attack can therefore cause significantly more damage than would be the case for a user with restricted rights.
Administrators and developers, however, require completely different content on the subject of cyber security. That is why there are two special training courses, Cyber LABs for Administrators and Cyber LABs for Developers, which address precisely these requirements and contents.
Our IS-FOX Cyber Security trainings have been developed by our in-house Cyber Security specialists. And this difference can be seen in the content. At least, that's what our customers say.
Our e-learning courses are suitable for small, medium and large companies and can be integrated into your own learning management system (LMS) or operated via our IS-FOX Cloud. Adapted to your company's guidelines and corporate design, of course.
Our content speaks for itself. That's why we show our demos completely without obligation and without annoying disclosure of contact details. For our interested parties and customers we also have a protected demo area with all content.
Technical and digital products used or manufactured by companies and distributed to end customers are part of supply chains. These, in turn, are popular and frequent targets of various types of cyberattacks, as it is not uncommon to be able to harm multiple parties simultaneously and thus capture more. Imagine tampered or insecure chips that end up being built into company computers and cell phones ... pretty nasty outcome.
For these products, the draft requires that appropriate cyber security measures, appropriate to the risk involved, be implemented as early as the design, development, production phases and also during commissioning and use. A distinction is made here between so-called low-risk and high-risk categories. However, we are still in the implementation phase here. The success of the CRA depends not only on its specifications being practicable and implementable, but also on whether a company is aware of its vulnerabilities and has the appropriately trained personnel available - including the indispensable cyber security awareness.
People are clearly at the center of this ever-increasing, though not new, threat. As the interface between private and professional information, they often offer a direct route to a multitude of data. This presents companies with a huge challenge, because it is not only systems and devices that need to be up to date with the latest security standards, but also their employees.
The Covid 19 pandemic in particular has spurred a tremendous increase in remote working. Many businesses and households are challenged to bring their premises and equipment up to a cybersecurity level as quickly as possible to sufficiently protect them from internal and external attacks. As the trend of remote working continues, this protection must be provided not only in the short term, but also in the long term. This is often not so easy, especially when working from different locations with third-party Wi-Fi networks and the like.
A few tips:
Always keep your system and anti-virus scanner up to date and do not store any work-related information on private devices or networks. Also make sure you always lock your computer, lock sensitive documents in a filing cabinet and avoid theft of your devices and insecure public Wi-Fi networks when working remotely.
As cyber criminals become more specialized and do not back down from virtual aggression, a stable and protected infrastructure is becoming increasingly important. This is not only the case in highly sensitive sectors such as medicine, healthcare and aviation security.
Politicians are largely aware of this and are working on new laws and regulations that companies must adhere to. In Germany, there is also the KRITIS umbrella law, which sets minimum requirements for critical infrastructure providers to make the overall system more resilient. For companies that want to have their information security certified, there is ISO 27001, for example.
This is technology that companies can actively use to protect themselves and their employees, as it is currently considered the highest authentication standard. But even here, caution is advised: not all methods of MFA are equally secure. Program-based tools such as security keys and app-based variants have a higher level of protection than phone-based ones, as criminal actors can sneak in relatively quickly and easily here. This can have troublesome consequences, especially in online banking or cloud service sharing. Besides, a second factor also does not protect against social engineering or targeted phishing attacks. Here again, it is a matter of awareness among employees.
Speaking of phishing: With an all-time high of around 300,000 attacks - in 2019 alone - phishing has become one of the most common forms of cyberattacks. So, it was only a matter of time before new variants would emerge here.
Smishing, for example, involves sending convincingly authentic-looking SMS and text messages from alleged postal services, for example, in order to trick potential victims into disclosing private information. Another new variant is vishing ('voice phishing'), in which automated telephone calls are made in an attempt to persuade the recipient to hand over access data, etc.
Even more perfidious: in spear phishing, cybercriminals even go so far as to enrich their email scam with publicly available information (e.g., from social media) in order to specifically target certain individuals for deception. This can even go as far as becoming a social engineering attack. The scams are on the rise, and so is the threat to all users.
There's no getting around the current trend of artificial intelligence - and no discussion about it either. The debate is heated: Opportunity or danger? The same applies AI with regards to cyber security. Here, too, AIs can be seen both positively and negatively. Companies that use artificial intelligence to enhance the protection of their data, infrastructures and systems can fend off potential attacks in an automated manner, or at least detect them more quickly and mitigate them considerably in financial terms.
At the same time, of course, criminals have also jumped on the AI train and use it for their own purposes, such as datapoisoning and ransomware.
No matter from which perspective you look at artificial intelligence - one thing is certain: it will have a major impact on developments in cybersecurity in the future.
What about devices that are neither computers, phones, nor servers, but are still connected to the Internet? Just think of smartwatches, voice assistants, smart cars, smart refrigerators. They are all part of the rapidly spreading digitization, spurred by the work-from-home trend.
The endless proliferation of devices naturally increases the risk of cyberattacks, as they significantly increase the attack surface. To make matters worse, these devices have various vulnerabilities - for example, a lack of storage capacity that barely leaves enough room for firewalls and antivirus software.
They have proven extremely useful - especially during the pandemic - as multiple users can access data from different locations. This makes the cloud efficient, cost- and space-saving. However, cloud services must be well configured.
But that's not all: employees must also be aware of which cloud services are allowed to be used. When users start using cloud software on the Internet themselves, insecure interfaces or incorrectly configured cloud settings can quickly become a gateway for cyber threats.
Implementing secure cloud protection measures is essential for companies and requires a certain level of IT know-how and an understanding of internationally varying legal requirements.
Technology and processes are only as good as those who develop, support and ultimately use them. While the initial focus was exclusively on broad-based training on cyber security awareness, the trend in the future will additionally focus on training for specific target groups and their needs.
After all, the finance department will need a different form of training than an IT admin or executive assistant, and they in turn will need a different one than production employees.
In the rapidly evolving and expanding world of cyber security trends and technologies, it's not easy to keep an overview - at IS-FOX, we've made it our goal to incorporate cutting-edge information along with exciting and easy-to-understand content into our online cyber security e-learning courses, and we make it a priority to ensure that the modules can be customized at any time to meet the needs of any organization.
This is the best way to determine which technologies best suit you and which trends you are most susceptible to. There is something for everyone in our training courses! :)
Holen Sie sich einen Demozugang und lassen Sie uns in einem Webmeeting über Ihren Bedarf sprechen. Wir zeigen Ihnen, wie Sie die Cyber Security in Ihrem Unternehmen mit Mitarbeiter-Schulungen erfolgreich stärken können.

Modern and entertaining IT security trainings protect your company from attacks and their consequences.
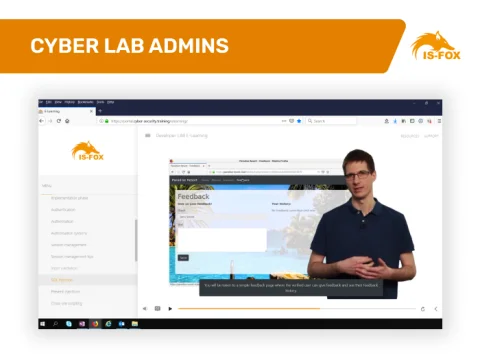
IT security training for administrators with interactive e-learning and hacking environment.

Up-to-date and modern online data protection training courses make your employees fit for GDPR. Find out more and book training now!

Online training for developers with a high practical component and your own LAB environment.

How to repackage familiar GDPR content into exciting online courses.

Find out how companies can properly motivate their employees to complete an e-learning course on cyber security, data protection or compliance.
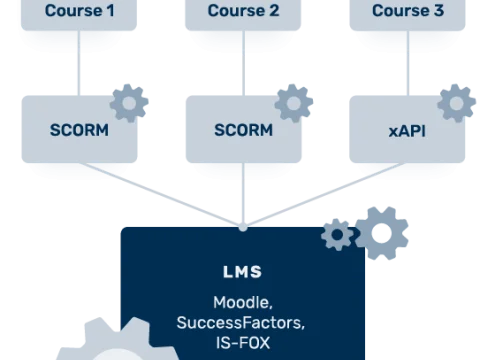
In this article, we explain the technical terms Scorm, LMS and e-learning course.
Technical settings and tips for LMS administrators