IT-Security Training for Administrators
Minimize attack risks with hands-on hacking e-learning.
Talk to an expertCustomers boosting their security with Cyber LABs
Better admins with security know-how than attackers with domain rights

Module 1: Secure Administration
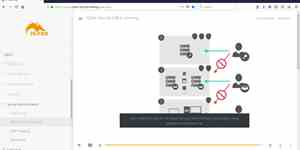
Die APT-Kill-Chain
Reconnaissance: Reconnaissance of the target area through research and scans.
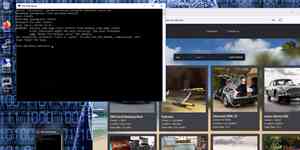
LAB exercise Scan of the environment with nmap and construction of the infrastructure map of the LAB.
Analysis: Detection of weak points with Nessus Report and development of the attack strategy.
Exploit Linux: Intrusion into Linux systems.
LAB exercise SSH Brute-Force with Hydra.
Exploit Windows: Intrusion into Windows systems.
LAB exercise Eternalblue (NSA Tool) with Metaspoit.
Lateral Movement: Take over of further systems and extension of rights up to Domain Admin.
LAB exercise 'Pass the Hash' with mimikatz and access to domain controllers with psexec.
Resilience
Patching & Hardening:
LAB exercise exploitation of Shellshock with meterpreter on Linux.
- Patch your systems promptly
- Harden your systems
Secure Administration:
LAB exercise usage of captured Linux passwords on other systems.
- Use different passwords
- Stick to RBAC and the principle of least privileges
- End RDP sessions properly (with explanation of RDP hopping)
- Use Password Manager, avoid hardcoded passwords
Detection & Response
Detection / Vulnerability Management: 'Detection is a must nowadays'.
- Introduction of the different detection instruments (NIDS, SIEM, EDR).
- Explanation SOC / CERT.
- Fix detected vulnerabilities promptly.
- Be vigilant yourself and watch out for anomalies.
In an emergency: correct behavior in an emergency with/without CERT.
- Isolate the systems
- Do not change system status
- Clearly document what you are doing.
Module 2: Cloud and AD Security
Security concepts part 1
Cloud security: The operating models in the cloud
Shared responsibility: the role of the admin and the cloud provider
Tips in the cloud: Clean account separation. PIM/PAM solutions / Jump Server. Various multi-factor methods. Private networks and IP restrictions
LAB exercise: Access to poorly configured cloud database through OSINT research
Defence in Depth: Attack vectors of modern ransomware gangs. Defence in depth based on various layers such as user awareness, perimeter security, network security, IAM, secure administration, secure software development, detection & response
LAB exercise: Linux SSH Bruteforce with and without MFA
Security concepts part 2
Importance of EDR: Differences to antivirus solutions. Use of EDR tools. Coexistence with antivirus software. Dealing with exclusions
LAB exercise: Effects of antivirus exclusions
Backup: Deadly sins in backup from a security perspective. The right backup strategy. Cloud exit and restore tests.
Logging in the cloud: Meaningful logs in the cloud
Patching & lifecycle management: The importance of patching: response time depending on criticality. Security tips for end-of-life systems.
Security tips
Authorisations on shares:
LAB exercise: Capturing privileged accounts through poorly set authorisations
- Awareness for assigning authorisations
- Inconsiderate share authorisations can create major security holes
NTFS and NFS: Setting permissions correctly
LAB exercise: Reading Linux shares
Participant Feedback

Cyber LABs - perfect for companies of all sizes
- SMEs do not have security specialists. Their service providers (system houses) also have a limited view and sell the products of their manufacturers.
- If individual security products are only used selectively, without a strategy and sometimes inadequately configured, then the risk of a successful attack is not sufficiently reduced. Such companies have no adequate defence against a professional attack.
- Successful attacks can be life-threatening for the companies affected. Numerous companies have already had to file for insolvency due to cyber attacks.
- IT managers learn how to turn individual security layers into an effective strategy. Many effective measures do not cost any additional money, they just need to be activated and properly configured.
- If companies take the tips and measures from the Cyber LABs to heart, they significantly reduce the risk of an attack threatening their existence.
- The cost/benefit ratio is excellent because companies are able to make a big leap in their cyber security with simple means.
- The measures defined by security are not implemented or are only implemented inadequately because there is a lack of understanding.
- Branches, national subsidiaries and branch offices in particular often have a significantly lower level of cyber security maturity and serve as a gateway for attackers.
- Many IT tasks are outsourced to external service providers that cannot be reached by the security teams.
- Cyber LABs can be used to sensitise and train system administrators internationally on the topic of cyber security, regardless of location, time or company affiliation.
- Existing security guidelines (e.g. hardening, patching, secure administration) are implemented better and faster, and resistance to security measures disappears.
- The level of security increases, especially in decentralised units and with IT service providers. This significantly reduces the risk of a successful attack.
A lot of good reasons
Frequently asked questions
The Cyber LABs are aimed at internal and external people who design, develop or operate IT infrastructure, i.e. IT managers, IT architects, application owners, software developers, system managers, administrators and support staff.
All "hacking scenarios" in the Cyber LAB are based on real APT attacks by current hacker groups and are therefore highly relevant. In the e-learning part of the Cyber LAB, we impart the knowledge of how professional attackers proceed - in the LAB environment, the participants are allowed to implement the knowledge they have learnt in the LAB themselves. They slip into the role of the attacker and work through a typical "kill chain". This change of perspective trains security awareness for potential vulnerabilities and promotes secure behaviour.
IT administrators understand the approach of modern attackers and learn to see cyber security as a concept and not as a collection of security products. Numerous practical tips enable them to significantly strengthen the security of their infrastructure through configuration, the use of on-board tools and security-conscious behaviour.
IT decision-makers in small and medium-sized companies will understand how cyber security works as a concept, which measures have priority and why the mere use of individual security products does not lead to the desired protection. This enables them to make better and more efficient decisions about the use of security tools and to better categorise the marketing promises of individual manufacturers.
Decentralised IT administrators understand the approach of modern attackers and learn why the cyber security guidelines of central IT are sensible and useful. They develop an understanding of the measures and no longer perceive them as annoying additional work from the head office. Security findings from audits and assessments are resolved faster and better, and the security level in the decentralised units increases considerably thanks to security-conscious behaviour.
HvS-Consulting, the company behind the IS-FOX brand, combines the expertise of a cyber security specialist and a learning specialist in a unique and special way. The technical security consultants and incident responders at HvS-Consulting are among the best in their field and experience attacks on companies on a daily basis, how the attackers proceed and which technical and human vulnerabilities they exploit.
The IS-FOX Security Awareness Team takes this special knowledge, reduces complexity and prepares it in a learning didactic way so that the training courses set the right priorities, are understandable, contain practical and realisable tips and are fun to attend.
Traditional, non-specialist learning specialists do not understand the complex content of cyber security and therefore cannot prepare the content optimally. Security specialists are too deep in the subject matter and are usually unable to convey this expertise in a simple way. The "magic" of the courses is created by this unique combination of security and learning specialists in one company.
In the LAB, participants can put the knowledge they have learnt into practice. The LAB for administrators simulates a company network with several prepared Windows and Linux systems, totalling 8 server systems. It contains up-to-date attack tools and assistance.
Option "Shared LAB environment"
You get access to one of our shared LAB environments in Microsoft Azure. Your participants share the LAB with other customers. Each customer can access the shared LAB environment with a maximum of 2 simultaneous users. A shared LAB environment is ideal if you want to train a small number of participants over a longer period of time (e.g. 50 participants in 1 year). Typical scenarios are smaller companies with few IT employees and larger companies that want to offer training to new employees on a permanent basis.
Option "Own LAB environment"
You receive one (or more) exclusive LAB environments in Microsoft Azure for your participants. They access the LAB environment(s) together. You can choose between 2 LAB sizes: "Standard" with 5 or "Enterprise" with 25 simultaneous users in the LAB. A dedicated LAB environment is ideal if you want to train a large number of participants in a short space of time (e.g. 200 participants in 3 months). A typical scenario is the initial training of all IT colleagues.
As standard, the learning units (the courses) are offered fully synchronised in German and English. On request, the learning units can be subtitled in other languages for an additional charge. The LAB environment is always in English.
You can use the Cyber LABs as a rental licence and choose between a term of six and twelve months. A six-month extension is possible.
Yes, the learning units can be integrated into your own LMS via "SCORM Streaming". As a customer, you will receive a learning package in SCORM format for your LMS. Although the content is retrieved ("streamed") via the IS-FOX Cloud, the course behaves identically to an "internal course", i.e. course administration, invitation management, booking of success, etc. takes place in your LMS.
The LABs and the associated administration (the "LAB Portal") contain a great deal of technology and logic and therefore cannot be operated in a customer's own Azure tenant. However, you can store the link to your internal LMS in the LAB Portal in order to establish a transparent connection.
Yes, that is possible. In order to better map your maturity level and your internal processes, we have created various jumping-off points where you can choose from ready-made modules or refer to your internal guidelines.
Yes, all courses include a follow-up test in multiple-choice form. After successfully passing the test, participants can download a certificate as a PDF.
The tracking dashboard is a matter for the learning management system. Our LMS naturally offers invitation management, participation tracking and corresponding statistics.
Yes, thanks to our expertise in incident response and forensics, we are always up to date with the latest technology, security vulnerabilities and attack vectors. We regularly pour this expertise into new content for your awareness target groups.
Yes, thanks to the many, sometimes optional, explanations and assistance in e-learning and in the LAB environment, we offer support where it is needed and avoid unnecessary explanations where they are not required. In addition, we offer a support service that provides your participants with help and advice should something not work.
Webinar: Cyber LAB Cloud security for admins
Increase your IT team's awareness of secure cloud systems and backups with Cyber LAB training.
Register now for the 15.10. (it's free!)