
Customers, who trust in our live events:
Customers, who trust in our live events:
Abus, Allianz, Amadeus, Bosch, Ergo, Evonik, Finanz Informatik, the airports DUS, CGN, FRA, HAM, MUC, ZRH, Geberit, Generali, Giesecke & Devrient, Groz-Beckert, Helmholtz Zentren, Henkel, Hornbach, IATA, LBBW, Lanxess, Loacker, Lufthansa, Munich RE, Osram, Otto Fuchs, Pro7Sat1, Rational, Rewe, Rohde & Schwarz, Saar LB, SAP, thyssenkrupp, ZF Friedrichshafen ... and hundreds more.
Keynote, security day, customer event
We don't hack Bluetooth interfaces, we hack people:

As good as an in-precense event
No boring “online webinars” but real virtual live events:


Target group-specific formats, always up-to-date
Phishing is and remains the top threat to companies and individuals. Phishing generates more revenue worldwide than drug dealing. In this interactive event, you will learn about various attack scenarios through practical demos and receive tips,
Through interactive online surveys and discussions, we actively involve you and you can apply your knowledge immediately.
Welcome to the next generation of phishing methods: Text messages, WhatsApp, QR codes and voice phishing. In this interactive event, you will learn how criminals are able to circumvent even modern technical protection measures such as 2-factor authentication and how you can effectively defend yourself against them.
We will show many practical examples of real phishing attacks and interactively involve you and the entire audience through online polls. With our defense tips, you will become an effective shield against cyber threats, both at work and at home.
Cybercrime generates more money worldwide than drug and arms dealing. Spying on access data (phishing) and encrypting information and systems with subsequent ransomware are currently the biggest cyber threats to companies. But how do attackers actually choose their victims? How are companies infected? And what crucial role do you play as an employee? In this event, we will use live demonstrations to show you
Through interactive online surveys and discussions, you are not just a spectator, but become part of the action.
Ransomware attacks - encrypting information and systems and then holding companies to ransom - are the biggest cyber threat today. But how do attackers choose their victims? How do companies get infected? And what is your role as an employee?
Immerse yourself in the world of ransomware and learn through live demos and real-life examples how quickly the professionals break through their victims' defenses, how ransom negotiations work and whether you as a company should pay.
Companies are not without a chance! Learn the elements of an effective cyber security strategy and the simple steps you can take to make a fundamental contribution to successful defense. We use interactive surveys to engage you and the audience.
Passwords are annoying! Too many, too complicated! But what can you do? Can you trust password managers? And what are the real benefits of multi-factor authentication? Your life with passwords will be easier after this interactive session. Learn with exciting live hacking demos
Through interactive online polls and discussions, you will be actively involved and can apply your knowledge immediately.
Psychological tricks and deception are becoming more dangerous thanks to artificial intelligence (AI). In this exciting course, you will learn from numerous examples and live demos,
Of course, we will also provide you with practical tips to help you identify and defend against these threats. You will be actively involved through interactive polls and will be able to apply your knowledge immediately.
With numerous live hacking demos, this live training offers not only exciting insights, but very practical tips to take your home cybersecurity to the next level.
We will actively involve you in the live event with practical examples, interactive online polls and direct Q&A sessions.
This live event will give you exciting insights and practical tips on how to take your home cyber security to the next level.
Through interactive online surveys and direct Q&A sessions, you will become part of the event and can ask the questions you always had about security.
Dive into the world of cyber security and learn how cyber criminals threaten companies and individuals. Through live hacking and demos, we will demonstrate modern attack techniques at first hand and teach you all the basics you need to successfully fend off such attacks. You will learn
Through interactive online surveys and discussions, you are not just a participant, you become part of the event.
It depends...
Of course, a real face-to-face event with social interaction and informal conversation remains the undisputed number one for human communication. But it comes at a price. Venues need to be booked and delegates, speakers and departments need to get there. A 2-hour event can often take between 3 and 8 hours, depending on travel time. Virtual events are much more economical and environmentally friendly and, since Covid, are now fully accepted.
We underpin our training courses and keynote speeches with live demonstrations or impressive live hacking elements. Examples:
Face-to-face training takes place exclusively on site, ‘in presence’. A virtual live event can take place as a Teams meeting, Webex event or stream. It is not a recording, but a live event. This enables interaction through online polls, discussions, Q&A sessions, chats, etc.
The results are almost comparable in quality. Above we have explained which format to use and when.
This is not an either/or decision. Real behavioural change occurs when you have multiple contacts with the target group via different channels.
Both formats have their purpose.
We are generally flexible, but have ‘best practice’ formats between 30 minutes and 2.5 hours that have proven their value over the years, depending on the topic and the target group. Live hacking events for managers are often shorter, as this target group only has limited time. A break should be planned for events lasting longer than 2 hours.
In principle, yes - if the participants actually take part.
We offer our live hacking events in German and English.
Yes, this is possible for an extra charge. However, we do not recommend this, as a live event thrives on its interactivity. Instead, we recommend offering additional dates or relying on replicable measures such as e-learning, videos or the intranet.
Yes, we can customise our standard content to your company and your specific topics at any time. We take into account your policies, such as password rules, and explain the proper reporting channels.
We are also happy to include specific examples of attacks from your company.
And for all those who dare, we can also run a tandem event with security specialists such as CISOs, ISOs or Cyber Defence Centres. We explain how the attackers proceed, you explain how you defend against them.
Live hacking events are suitable in various ways
Security awareness campaigns are our speciality. Feel free to contact us.
Yes, both in our best-practice standard and by individual arrangement.
Examples:

Our phishing tests measure, sensitize and train in one go.

Modern and entertaining IT security trainings protect your company from attacks and their consequences.
IT security training for administrators with interactive e-learning and hacking environment.
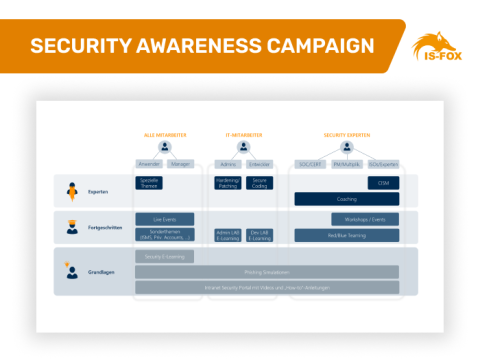
Sensitize your employees, managers, administrators and developers with a holistic cyber security awareness campaign