2.000+ customers place their trust in us, from startups to large companies
Not just another phishing tool provider
Actual security awareness
There are countless providers of phishing simulation software these days. They all claim that if you use their software, you have everything you need. We see things differently. Security awareness is much more than just a regular phishing email followed by a short learning session.
- Continuous phishing tests do address an important attack vector. But only one.
- We see phishing simulations as one of many measures in a comprehensive security awareness campaign.
- If you still "only" want to do a little phishing, we will of course do that too, even if it means losing some momentum.
The perfect addition for security awareness
Combine phishing simulations with a full-on e-learning or live event
Phishing simulations can be very useful as a "communicating element" for other awareness measures, e.g.
- As a wake-up call at the start of a security awareness campaign.
- As an invitation to a cyber security e-learning course, a (virtual) live event or an on-site security day.
- To communicate new reporting channels for cyber incidents.
- To communicate the new security intranet.
For successful security awareness, various measures are combined for a comprehensive campaign. We have a great deal of expertise in this area and are happy to show you what's possible.


More than just a phishing tool
Full-service phishing simulations and true awareness
What, who, why, when?
We define the objectives of the phishing simulation together:
- Who do you want to test? All employees or only certain groups? Regions? Departments?
- How often? Monthly? Quarterly? Annually?
- Why? As a wake-up call for everyone or rather as continuous training? Or both?
- What granularity should the evaluations have? At department level? Or by country?
- How many resources/know-how do you have in-house? Do you also want to provide your own services?
We also advise you on the technical and legal advantages and disadvantages of various concepts and work with you to develop a viable concept within a few hours.
A fool with a tool is still a fool
Grady Booch, Software Engineer
In the second step, we recommend the most suitable tool according to the conceptual parameters.
GoPhish
The open source software GoPhish is simple and inexpensive. Ideally suited for “classic” phishing simulations, such as clicking a link, entering a password or executing an attachment - including QR code phishing. We can easily carry out 2 to 5 phishing simulations per year, even for tens of thousands of recipients.
Cyberdise
If the simulations are to be randomly distributed throughout the year, we use this professional phishing simulation software from Switzerland. Distribute different scenarios throughout the year, QR code phishing, etc. Anything is possible, nothing's mandatory.
Not too easy, not too hard
We select the most suitable scenarios together. We use our numerous best-practice scenarios or create individual scenarios for you.
We adapt the phishing email, the landing page and the resolution page visually and in terms of content to your company and the specific target groups.
And we make sure that the scenarios are realistic, coherent, yet recognizable - otherwise phishing simulations create exactly the opposite of what we actually intent.
All-in-one service
We create the phishing server including the phishing simulation software. We integrate the chosen scenarios, register the required domains and test the technical functionality.
On the customer side, you only need to ensure once that emails are received (“whitelisting”) and that the simulation is not blocked. We have extensive information on whitelisting on our support pages.
After a final test, we send the emails to the defined target groups at the agreed times and monitor the process.
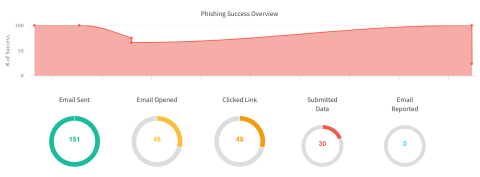
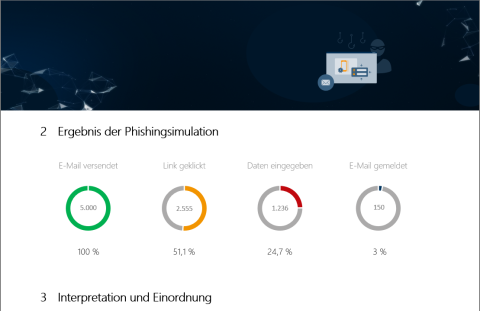
At the end, you will receive an (usually anonymized) evaluation of the “success” of each measure in a professional report, with graphics and benchmarks: how many emails were sent, how many were opened, how many people clicked, how much data was entered. Additional filters (country, region, department) can be defined on request.
Telling a whole story
We ensure that the phishing campaign is integrated into the existing or planned awareness communication in the best possible way.

Because phishing simulations have a lot of value besides just training for phishing specifically. If possible, we should not let this momentum go to waste.
Single campaign
Let's just go phishing.
Select your package, define your scenario, whitelist our emails and you're good to go! We offer a full service - with established best-practice scenarios and learning units and without any expensive annual software fees.
Individual phishing
Tailored to your needs.
Do you want to test continuously? Target specific groups? Simulate certain scenarios or convey certain messages? In combination with a live event, e-learning or as part of an awareness campaign?
Phishing with experts
Our security consultants, incident response specialists and social engineers know which attacks are successful in real life. That's why our scenarios are very realistic and not just “clumsy attempts” using the same senders every time.
Added value through communication
Phishing simulations are an excellent communication tool for conveying security messages if they are intelligently embedded in security awareness measures. Phishing simulations alone only reduce a single risk.
All-in-one service
We don't just want to sell you “that one software”, but always choose the solution that best suits our customers' needs. Sometimes this is simulation software, but often it is not. This is not only efficient, but also easy on the wallet.
We define a campaign as the creation and execution of a phishing simulation with a specific scenario to a specific target group on a specific day, for example the execution of the “Microsoft Teams invitation” phishing simulation to all employees worldwide on May 5.
The scenario is the respective “phishing scam” used in a campaign, for example “Microsoft Teams invitation” with user name and password input.
We create a dedicated phishing server including the phishing simulation software. We integrate the selected scenarios, register the required domains and test the technical functionality.
You only have to ensure once that the IP address is not blocked (“whitelisting”) and that the emails are accepted and delivered by your email server.
You send us the e-mail addresses of the recipients, including any evaluation parameters (location, department, etc.). After coordination, we send the e-mails to the defined target groups at the agreed times and monitor the process.
At the end, there is a (usually) anonymized evaluation of the “success” of the measures: How many emails were sent, how many were opened, how many people clicked, how much data was entered. Additional filters (country, region, department) can be defined on request.
For more detailed evaluations, we send the results in the form of an Excel file, which can then be further analyzed and pivoted.
Our credo: We don't want to investigate the misconduct of individuals, but rather sensitize users to the dangers of phishing attacks.
That's why our standard is: we know, our clients don't.
In order to be able to correctly evaluate click rates, phishing simulations generate individual emails with individual links. This means that clicks are recorded on a user basis.
Unless explicitly agreed otherwise with the customer, we do not provide access to the backend system, but aggregate the data into anonymous statistics and transmit these as part of the evaluation. Rough filters (e.g. by department, region or language) are of course still possible. We do not normally pass on any information that could be used to infer the behavior of a single individual.
No! We ensure that in all simulations that require passwords to be entered, these do not leave the user's end device. We do not transmit any passwords entered.
Of course. German security specialist, German data center.
We process email addresses and names in a phishing test. Although this information is associated with a low risk of damage in a data protection risk assessment, we naturally conclude a contract for order processing in accordance with the EU GDPR. The individual results of a phishing simulation are deleted after creation and transmission of the evaluation of the respective campaign.