
Phishing with Microsoft Teams
Criminals try to carry out phishing attacks via fake links and malicious attachments in Teams chats.
Criminals try to carry out phishing attacks via fake links and malicious attachments in Teams chats.

Many people only think of phishing in terms of emails. But in fact, it's all about victims clicking on a link or opening a file with malicious code, regardless of the app. Of course, phishing also works in text messages and chats. And currently, criminals have discovered Microsoft Teams for themselves.
In Teams, you can be contacted by external people in chat, which is definitely beneficial for communicating with customers and suppliers. However, attackers are now increasingly using this function for phishing attacks. To do this, they register with Microsoft Teams under a fake name. They then research information in social networks and write to their victims via Teams in a very targeted manner, as a supposed supplier, customer or very often as a recruiter.
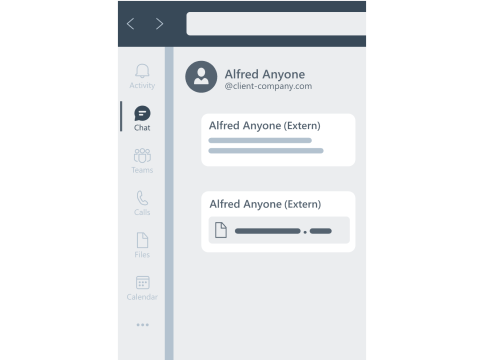
Microsoft has actually disabled the "send files via chat" feature for external communication partners. Well, actually. But security researchers have found a way to reactivate this function after all. This means that criminals could also send malicious files to their victims via Teams. "I have an incredible job offer for you, it's a perfect fit, let me send you more info in a file". This is exactly how one or the other ransomware encryption has started.
Microsoft has acknowledged the vulnerability with a shrug and has not commented on whether it will be closed in the near future.
Please be particularly vigilant if external third parties send you a link or maybe even a file in chats, even and especially if the person is just talking to you on the phone. The attackers build up a plausible story through research, call their victims, sometimes even with a video, engage them sympathetically in a conversation and then send the link or the file in passing. In such a situation, the victims do not even think about a possible attack and therefore do not pay attention to possible indicators. And that's exactly what the criminals are counting on.
At least, Teams clearly marks external persons with an "External" behind their name. This makes it very easy to detect attacks in which the attacker is posing as an internal colleague.
We cover the topic of phishing with Microsoft Teams in two of our cyber security e-learning nuggets
As always, you can find these chapters in our demo area.
Boost awareness of cyber security, data protection, compliance, and workplace safety with engaging content that truly sticks.

How to repackage familiar GDPR content into exciting online courses.

Find out how companies can properly motivate their employees to complete an e-learning course on cyber security, data protection or compliance.
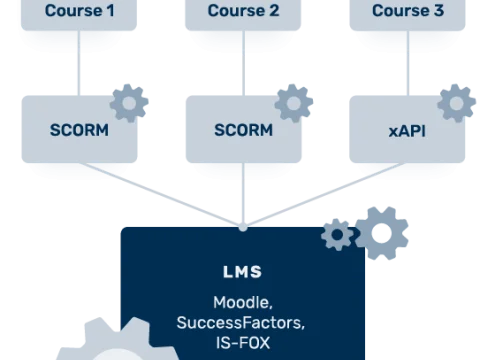
In this article, we explain the technical terms Scorm, LMS and e-learning course.
Technical settings and tips for LMS administrators